Vastflux – one of the biggest detected Ad Frauds!

source: own elaboration
Programmatic advertising has been breaking popularity records for several years now, and this year it is one of the most frequently mentioned online marketing trends. Its numerous advantages make advertisers invest exorbitant sums in it, but unfortunately its widespread use is a breeding ground for online advertising scams. This was noticed by the fraudsters behind the biggest detected advertising scam of 2022 called Vastflux.
The name Vastflux is a combination of „fast flow”, a type of hacker attack that uses the DNS evasion technique of constantly changing IP addresses within a single domain - and „VAST” (Video Ad Serving Template), a template that allows displaying advertisements in video players, developed by the Interactive Advertising Bureau (IAB), which was used in the attack.
How did the scammers behind Vastflux operate?
First, the group behind the attack tried to buy individual ad spaces in well-known mobile applications, posing as an intermediary acting on behalf of advertisers. According to Marion Habiby, a specialist at Human Security, a firm dealing with fraud and bot activity, who was the lead investigator on the Vastflux case – „They were not trying to hijack an entire phone, or an entire app, they were literally going through one ad slot”.
But of course, the scammers modified the ad before placing it in the acquired ad space. Malicious JavaScript code was added containing hidden instructions on which applications to spoof, how to do it and, above all, how to set the video player to play ... 25 ads at a time. An additional piece of code was added to digital advertising creations, enabling fraudsters to play up to 25 video ads at once one under the other and thus record up to 25 ad impressions instead of one that was actually visible to the recipient.
„It doesn’t stop with the stacked ads, though” - said Human Security - „For as many of those as might be rendering on a user’s device at once, they keep loading new ads until the ad slot with the malicious ad code is closed”.
This means that the creative not only served multiple ads at once, but also created „playlists” of them with a different URL and tracking code for each recipient to avoid a repetitive pattern. After seeing one marketing material (and supposedly viewing 25), another was generated, and another until the application was closed.
Detecting the scam wasn’t easy...
The fraudsters behind Vestflux were very careful - they left no trace on the device itself. „It’s quite genius because the minute the ad disappears, your attack stops, which means that you’re not going to be found easily” says Habiby. The scammers also gave the impression that the ad impressions came from many different apps when in fact only one was used and modified their ads so that they could control what tags are attached to the ads.
Device owners also had no idea what was going on, because although there were signs such as: the phone discharged faster, significant spikes in data usage or randomly turning on the screen, they were using proven applications and real ads were displayed to them.
On what scale was this Ad Fraud carried out?
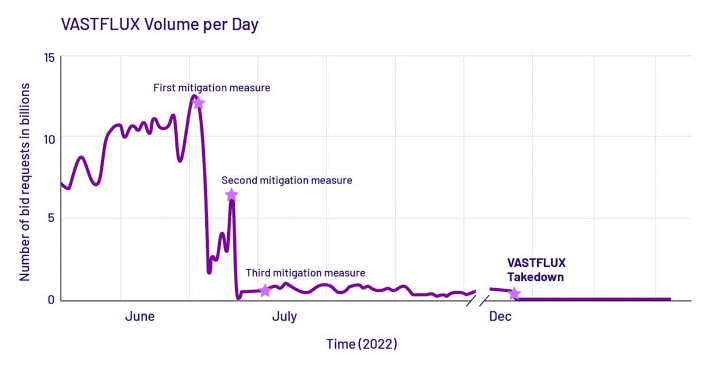
The attack took place on a massive scale - as many as 11 million phones were used (mainly iOS devices, although some Android devices were also infected), fraudsters falsified data on 1,700 applications and 120 publishers, and at the peak moment (June 2022) they sent 12 billion ad requests per day (see chart below from https://securityaffairs.com/). This generated huge profits for them, and significant losses for the unsuspecting principals.
„When I first got the results for the volume of the attack, I had to run the numbers multiple times” -says Habiby, describing the attack as one of the biggest and most sophisticated he has ever dealt with.
Detection of fraud
Vastflux, was accidentally discovered while investigating another ad abuse in the summer of 2022 by Vikas Parthasarathy, an expert working for the aforementioned Human Security, who noticed that the app was making an unusually large number of requests and was returning different app IDs.
The investigation lasted half a year and ended with Vastflux being blocked in December 2022, when the scammers decided to shut down the servers used for the scam. The Human Security company reported its discovery to Apple and Google, but didn’t disclose the identity of the scammers, because information about who was behind Vastflux and how much he earned from it is kept secret due to ongoing investigations.
Although the data on Vastflux is shocking, it is probably just the tip of the iceberg. Let us remember that this particular ad fraud has been detected and hence we have information about it. However, we have no idea how many similar and completely different advertising scams occur every day. All the more important is the active fight against advertising fraud, to which every entity dealing with online marketing should join.