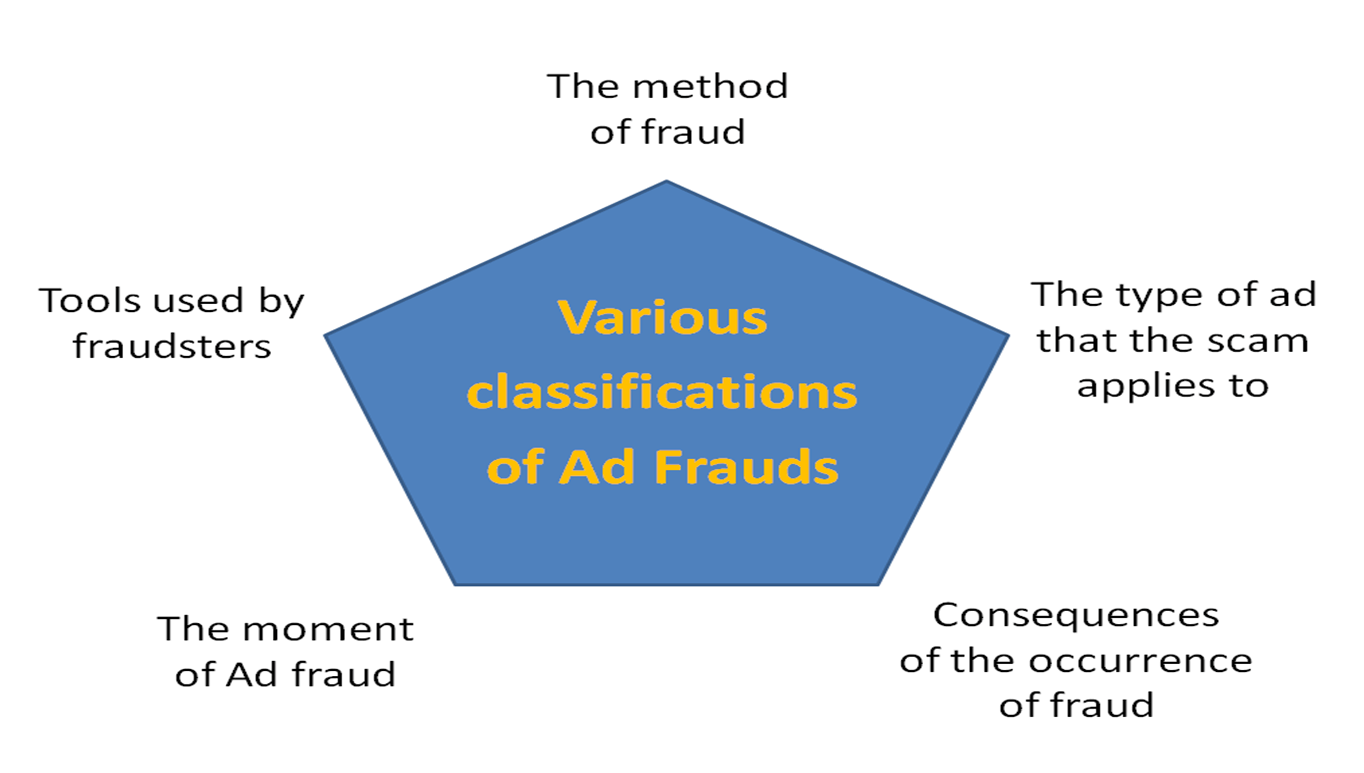
Various classifications of Ad Frauds
source: own elaboration
The term Ad Fraud, and therefore online advertising fraud, is an extremely flexible term covering whole categories of illegal activities that may harm advertisers - therefore it is impossible to give one definition. Additionally, the phenomena it concerns are very dynamic, they constantly take new forms and use modern technologies. For these reasons, giving one Ad Fraud classification is extremely difficult and certainly not going to be exhaustive - so instead of trying to create one classification, we will discuss a few of the most widely used ones.
Ad Fraud classification criteria
Although all Ad Frauds will be related to Internet advertising to some extent, there are many types of them. As a classification criterion, you can use the methods used to carry out the fraud, the tools used, the type of advertising that the fraud relates to, or the effects that they may have on advertisers. As for the criteria for classifying advertising fraud, we will discuss in this text:
- The method of fraud
- Tools used by fraudsters
- The type of ad that the scam applies to
- The moment of Ad fraud
- Consequences of the occurrence of fraud
Of course, even the 5 above-mentioned classification criteria doesn’t have to be exhaustive for this topic. Someone may say that it would be necessary to add additional categories here, such as who is the victim of fraud, the recipient of the advertisement concerned or the scope of the fraud. As we have already mentioned, the topic of Internet advertising fraud is extremely extensive and the discussion of every possible classification is a possible topic for book series, not for an article. Below we will briefly describe the different types of online marketing fraud based on the 5 classification criteria mentioned above.
- Method used by fraudsters
- use of real data without the consent of the data subjects - i.e. fraudsters using correct information, without having the appropriate consent from data subjects (such as transferring the data held to many advertisers simultaneously without informing data subjects about it, reusing old databases data without valid consents, etc.)
- impersonating the recipient of an advertisement - when the message doesn’t actually reach the recipient, and the scammer often impersonates him by taking additional activities on his behalf (fake clicks, fake ad views, fake application downloads, etc.)
- stealing conversions from an honest publisher - advertisers aren’t the only victim of online marketing scams, they can also be other publishers, fraudsters steal conversions generated by them and dishonestly assign them to themselves.
- Tools used by fraudsters
- Human Resources, including:
- entities acting on their own, i.e., for example, a dishonest competitor or an employee intentionally acting to the detriment of the company who personally commits fraud (clicking ads, filling in forms with incorrect data, adding false ratings, opinions and comments, etc.)
- outsourcing of human resources, i.e. Click / Recreation / Like Farms with employees, fake call centers or other forms of using other people to commit fraud
- Machines and programs, so above all:
- BOTs, i.e. automated programs that perform tasks assigned to them, often including impersonating people or imitating their behavior
- BOTnets, i.e. collections of devices infected with malicious software by the fraudster, thanks to which he can use them for his own purposes, often without the knowledge of the owners of the devices creating the BOTnet
- automatic Click / Open / Likes Farms, i.e. places generating artificial clicks, views or likes on a mass scale using machines and programs, and not human resources
- Mixed solutions, i.e. all methods of fraud using both human resources and machines.
- The type of ad that the scam applies to
- Advertising in Social Media, i.e. concerning artificial shares, fake comments, automatically generated reactions, as well as posts created by BOTs, etc., interestingly, in this group we can also encounter frauds committed on behalf of the advertiser
- Video ads, i.e. mainly false views of advertising videos, automatic sharing of materials by BOTs, etc.
- Ads in search results, banner ads - in this Ad Fraud group we can find Google Ads click spamming, as well as artificial clicks generated during affiliate marketing campaigns
- Ads in the Mobile channel, so mainly fake downloads and installations of applications for mobile devices
- Ads published on advertisers’ websites - such cases are, for example, contact forms filled in with incorrect data, fraud involving the artificial attribution of a given sale or conversion to a fraudulent publisher, even though the given activity was actually generated without the involvement of the fraudster on the advertiser’s website, etc.
- Ads on foreign websites - to this category we can assign any frauds committed on fraudulent websites, including the use of channels and forms of communication prohibited by the advertiser (such as motivated traffic, contests, etc.), creation of false websites with names and resembling to the original ones, etc.
- Moment of Ad Fraud
- The sender of the message, such as:
- broadcasting on surfaces other than those specified in the order (domain spoofing, broadcasting in prohibited channels, traffic buying, traffic from BOTs and false followers and fans)
- manipulating placements (multiplication of impressions and invisible emission)
- manipulating statistics (impressions and traffic from data center, spoofing mobile attribution, cookie stuffing and cookie dropping).
- Recipients of the message, including:
- improper presentation of the advertiser’s offer
- recycling of leads
- motivated traffic
- broadcasting advertisements, often without the user’s knowledge, on his device (including the insertion of advertisements on websites, zombienets, etc.)
- Advertiser’s landing page, i.e.
- false conversions, including incorrect leads and illegal transactions
- falsifying manifestations of involvement
- abuse related to product returns
- Consequences of the occurrence of fraud
- For the consumer, online marketing fraud can have the following consequences:
- financial - if the data of a given person has been unlawfully used to purchase products or services
- legal - data of which the consumer is the subject may be made available to other entities without his knowledge
- infecting the device - one of the main consequences of internet frauds for internet users may be the download of malware on the hardware, as a result the fraudster can take control of the device without the owner’s knowledge
- For the advertiser, the effects of fraudsters may be even more serious:
- financial - in the vast majority of cases, the consequence of ad frauds will be to expose the advertiser to costs that may constitute a significant part of their advertising budgets, financial losses are caused both by dishonest publishers who trick the advertiser (in the case of affiliate fraud) as well as result from the low efficiency of marketing activities also caused by the fraud (in the case of click spamming Google Ads or obtaining traffic from false sources)
- legal - if fraudster illegally used the data of real users, the advertiser may also face serious legal consequences
- image-related - it should be remembered that the advertiser may also fall victim to a fraud aimed at compromising the good name of his brand - fraudster may post online false comments, ratings and opinions, even on a mass scale.
This is an extremely important criterion because only understanding how fraudsters work can give an answer on how to stop them. They operate on the basis of various methods, but for the purposes of this study, we will mention 4 main categories, so:
- use of false data - when fraudsters use information that is fabricated or modified so that it becomes untrue (auto-filling in contact forms with false information, modifying existing phone numbers and email addresses, etc.)
However, understanding how fraudsters works won’t be complete if we don’t have information about the resources it uses. One of the classifications must therefore be precisely them. The tools used in online marketing fraud can be divided into three main categories:
Of course, one of the more obvious criteria for classifying Ad Frauds are the types of ads they are used for. So, we can distinguish scams related to:
This classification we have already discussed in the article devoted to the Whitepaper created by IAB Polska (link to the article). We can distinguish frauds related to:
In our opinion, the consequences of the occurrence of a given fraud are extremely important from the point of view of the advertiser and the consumer. We can divide them into those that will arise on the user’s side and advertisers.

